Privacy should be respected, not monetized.
The rise of digital advertising didn't just supplant the legacy advertising industries; it was built on an entirely new model of data mining every aspect of everyday life: relationship data, location data, financial details, purchases, health and fitness data and medical records.
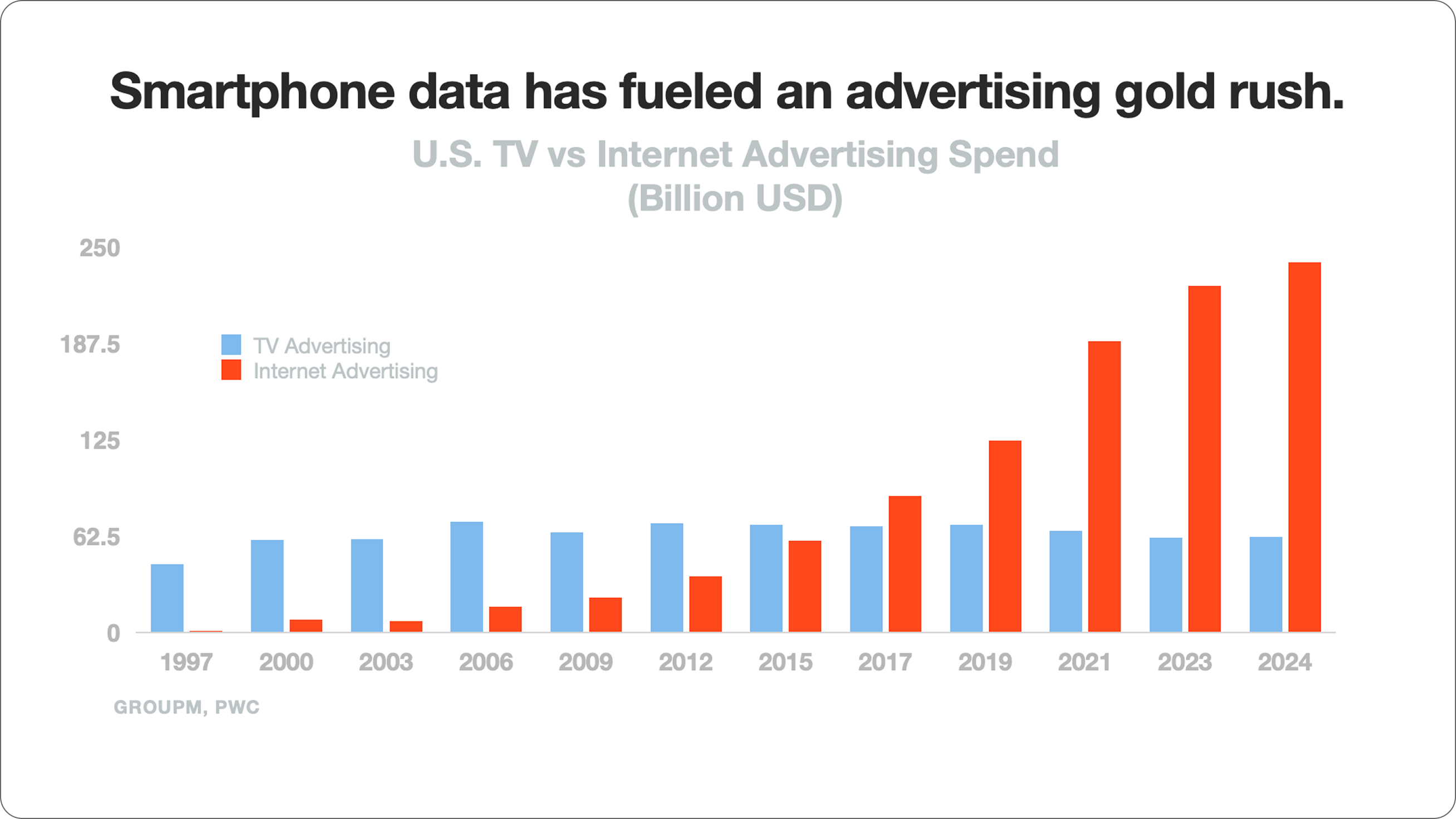
As AI progresses, Big Tech has set their sights on biometric data, individual DNA, our emotional responses – even human thought. It’s time to turn the tide.
How UP Phone Can Protect Your Data
We do everything on our smartphones; but the information they contain, and the digital trail they can leave, creates layers of risk.
Unplugged offers features to protect customers on each level.
-
App Derived Data
App Derived Data
For sale
Location, movement, relationships, beliefs, health information, financial data, shopping habits, photo data and apps.
Frequency
Hundreds of thousands of known third-party data-harvesting trackers extract hundreds of billions of packets of data across worldwide smartphone users every single day.
How it works
Data brokers and advertisers pay premium rates to enhance the targeting of their messages and to track you. For example, you may be shown an offer for a product when you are in the proximity of a particular store or business.
The pervasive nature of the data extraction economy is staggering in scale. Surveillance capitalism targets everyone and is exponentially more common than other forms of collection or interception. There are an estimated 7.2 billion smartphones in use globally, and a single user can be targeted for over a million packets of device-specific information in a given day.
This isn't just about advertisers; Governments, private investigators, hackers and any motivated actors can easily and cheaply purchase access to this same data. It has become a major threat to personal privacy and security.How Up phone protects
Firewall: Blocks third-party app infiltration and collection from opening connections with over 225K known data-harvesting servers.
De-Googled Android: UnpluggedOS is our own customized operating system based on the Android Open Source Project (AOSP). This means UP Phone runs most Android-compatible apps, but it is completely de-Googled and divorced from Google Mobile Services and all the surveillance and data capture in their ecosystem.
No logs VPN: Obscures IP address from website and apps.
Global Sensor Controls: Prevents apps from accessing the microphone, camera, bluetooth and other sensors at the operating system level.
Brave Browser: Browse and perform AI-assisted research privately with the default Brave browser on device.
-
Cell Carrier Records Request
Cell Carrier Records Request
WITH WARRANT AND WARRANTLESS
Location data, call logs, SMS and MMS records, transaction data
Frequency
From hundreds of thousands to over a million times per year.
How it works
Federal, state and local law enforcement agencies can obtain court-issued warrants and serve cellular providers to obtain location data, call logs, SMS and MMS content and other meta data. Whatever is written in SMS is readable by authorities. Sadly, anecdotal reports confirm that some people have gone to prison for incorrectly interpreted cell carrier records.
Under some circumstances, law enforcement and intelligence agencies such as the FBI, NSA and CIA are authorized under a lower standard to conduct warrantless surveillance and request cellular carrier information. This happens under court orders made by the Foreign Intelligence Surveillance Court (FISC). Customers are often not made aware of this activity.
The most controversial legal instrument is the National Security Letter (NSL). Using an NSL, the U.S. Government, most commonly the FBI, simply orders a business, ISP, telecom company or financial institution to disclose transactional information (non-content information) for a national security investigation. They can do this without court oversight and on their own certification. Also, the NSL is usually governed by mandatory non-disclosure. The recipient is prevented from informing their customer they received the letter.How Up phone protects
PAIRED WITH E2EE MESSAGING: Using the UP Phone with end-to-end encrypted messaging apps such as Signal, Threema, Session, Element and Briar instead of SMS texting prevents cell carrier databasing of the contents of your messages.
IoT DATA PLAN WITH POND MOBILE: Unplugged designed a custom data-only plan with Pond Mobile. This is available as a privacy-first cellular plan. With this mobile service plan, location updates are purged daily and Call Detail Records (CDR) are purged within one-week after the billing cycle, so the data is constantly scrubbed and does not exceed 37 days aging within the system.
BATTERY DISCONNECT: The physical Battery Disconnect switch disengages UP Phone from all its electronics. Communication with carrier infrastructure is terminated. Big Tech competitor devices continue to connect with cell towers even when the phone is not in use or is turned "off". UP Phone does not. Off truly means off.
-
Device Seizure
Device Seizure
REQUIRES WARRANT EXCEPT AT BORDER CONFISCATION
Frequency
Hundreds of thousands of times per year in connection with criminal investigations and arrests.
At border: Tens of thousands of basic searches. Less than 15K enhanced searches per year.
How it works
Law enforcement may physically seize a smartphone during an investigation if there's probable cause to believe it contains evidence.
While the device can be seized as part of an arrest, a warrant is almost always required to search its digital contents, Following seizure, forensic experts create a bit-for-bit copy of the data to analyze evidence while preserving the original, ensuring the process is legally sound and admissible in court. This process reveals unencrypted communications, can expose passwords, all local files, and potentially access to online accounts.
The United States border and international airports run under a different set of operating procedures. The Customs & Border Patrol (CBP) can seize a cell phone and ask you to unlock it for a basic search or confiscate it for longer. Know your rights. The rules are different for U.S. citizens versus Green Card Holders or visa holders or travelers from visa waiver countries.How Up phone protects
LOST MODE: Timed security feature for when you've been away for a while. Reword to make clearer
SCHEDULED REBOOT: Set the times you want your device to reboot and clear the cache.
EMERGENCY RESET: False pin to wipe phone in the event of its seizure.
FINGERPRINT LOCK: You can set up your device to unlock with your fingerprint to prevent unauthorized access. Fingerprint versus facial recognition -
Remote Penetration
Remote Penetration
Classified
Identifiable information of close-proximity devices plus text, call and data content
Frequency
Unknown, but the equipment used for remote penetration is highly technical and expensive. There is a market with multiple players offering hardware designed for authorized law enforcement, intelligence and military applications.
How it works
Although rare, highly-financed cybersecurity operators, usually working for national governments, can use software like Pegasus to remotely penetrate and control the software (and even hardware sensors) of a device.
Other sophisticated tools for remote penetration include pen registers, trap-and-trace devices such as IMSI catchers/StingRays and KingFish phone trackers. Active IMSI catchers are illegal for "unauthorized" individuals to possess. However, motivated actors in intelligence agencies, foreign governments and even rogue criminal organizations still use these technologies. A passive IMSI catcher does not transmit any signals itself. Instead, it works by silently monitoring and capturing cellular transmissions broadcast by mobile phones as they communicate with legitimate cell towers, similar to how an FM radio receives signals.
Even remote keyloggers placed by malware or third-party app infiltration can give motivated actors the ability to penetrate your device.How Up phone protects
BATTERY DISCONNECT: Prevents the phone from being tracked electronically or for remote software to enable sensors.
USB DATA BLOCKER: Blocks your charging port from moving data if the charging station you are using has been compromised.UNPLUGGED ANTIVIRUS: Blocks and scrubs tens of thousands of known malware and virus attackers and keylogger embedders. Constantly updated as new exploits become known.
2G NETWORK SHUTOFF: Older cellular network technologies are particularly vulnerable to interception. All smartphones are designed to jump between older and newer network technologies to route data efficiently. UP Phone includes a 2G Network blocker which is the most vulnerable wireless band.
Privacy isn’t just our concern—the evidence is all around us.
ACLU
"Americans should not have to choose between using new technologies and protecting their civil liberties. We work to ensure a future in which the Fourth Amendment ban on unreasonable searches extends to digital property and your data is your own."
Pew Research Center
"A majority of Americans say they are concerned, lack control and have a limited understanding about how the data collected about them is used. This is true whether it’s the government or companies using their data"
-Colleen McClain, Michelle Faverio, Monica Anderson and Eugenie Park for Pew Research
Electronic Frontier Foundation
"Assigning a dollar value may give the false impression that, at a value of $5, $30, or $200 for your personal information, the data collection companies’ conduct is no big deal. But a specific piece of information can be priceless in a particular context. Your location data may cost a company less than a penny to buy, yet cost you your physical safety if it falls into the wrong hands . . .
"Our information should not be thought of as our property this way, to be bought and sold like a widget. Privacy is a fundamental human right. It has no price tag. No person should be coerced or encouraged to barter it away."
-Hayley Tsukayama, Electronic Frontier Foundation
Digital Progress Institute
"Although our right to privacy from our government is well established, that is unfortunately not the case with respect to companies. With the allure of free services, we provide details about our most intimate selves to trillion-dollar tech companies who, in turn, make an enormous profit off the data they collect.
"They know everything about us. What we like to eat. When we sleep. Where we live. Where we are. Our beliefs. Our fears . . .
"The problem is not just that they sell our data to third-party advertisers but also to those who use our data to create fake images, curate biased newsfeeds, conduct elaborate scams, and even engage in espionage. In short, we are not in control, and Americans are right to be concerned."
-Joel Thayer, President, Digital Progress Institute in testimony before U.S. Senate Judiciary Committee
ACLU
"Today, a massive amount of revealing personal information is stored on our computers and cell phones, and “in the cloud,” on Internet-connected servers hosted by the scores of online companies whose products and services we use daily.
'Modern computers, including cell phones, differ in both a quantitative and a qualitative sense from other objects that might be kept on an arrestee’s person. . . . [M]any of these devices are in fact minicomputers that also happen to have the capacity to be used as a telephone. They could just as easily be called cameras, video players, rolodexes, calendars, tape recorders, libraries, diaries, albums, televisions, maps, or newspapers.' Riley v California, U.S. Supreme Court
"Digital information generated by today’s devices and services reveals individuals’ private matters far beyond what one could learn from physical analogs. A device the size of a human palm can store practically unlimited quantities of data. For example, sixteen gigabytes of information—the standard capacity of a smart phone around the time the Court decided Riley—'translates to millions of pages of text, thousands of pictures, or hundreds of videos.'"
-Jennifer S. Granick, Surveillance and Cybersecurity Counsel, ACLU
in her paper: Make Warrants Great Again: Avoiding General Searches in the Execution of Warrants for Electronic Data